Enterprise-Grade PC Security Solution
OfficeKeeper
- 7-in-1 Security Platform
- Industry-Leading Adoption Rate
- Flexible Deployment Options

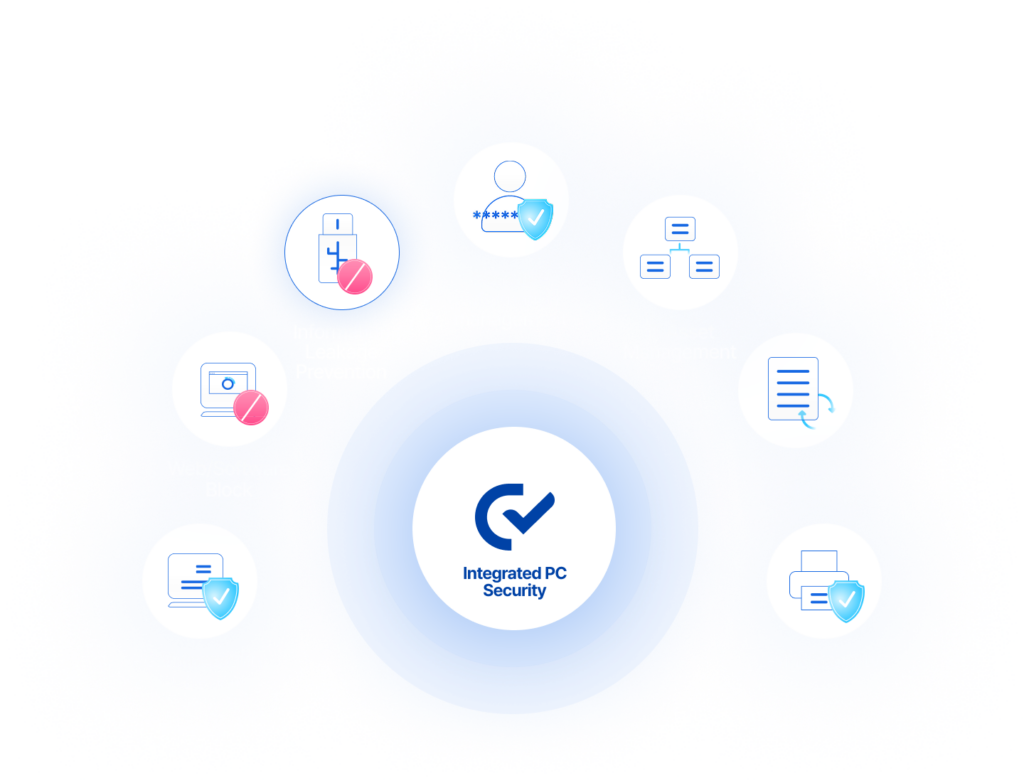
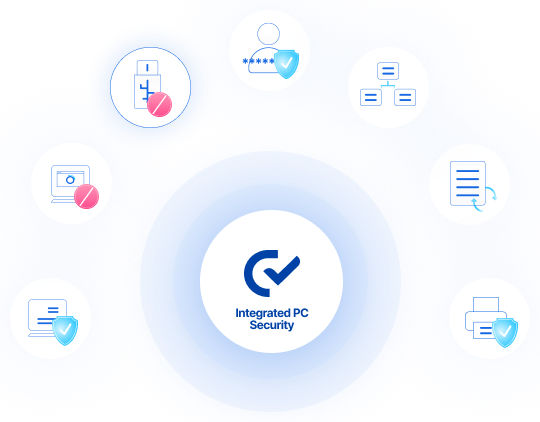
Manage 7 Security Functions in 1 Agent!
Korea's Leading Security Solution with the Highest Market Share
Data Loss Prevention
Control file leakage through external media (USB, external HDD) and communications (email, messenger)

Sensitive Information Management
Encryption and export control of confidential information and personal data documents

Web/Software Blocking
Block access to non-work-related software and potentially harmful websites

PC Security Assessment
Diagnose PC vulnerabilities based on 17 security standards from the National Intelligence Service
IT Asset Management
Manage software licenses, hardware inventory, and other IT assets efficiently

Document Backup
Automatically back up files stored on PCs and maintain records of exported files

Print Security
Prevent critical information leakage through print controls and document watermarking
Solve Your Corporate Security Issues with OfficeKeeper's 7 Key Features
Data Loss Prevention (DLP)
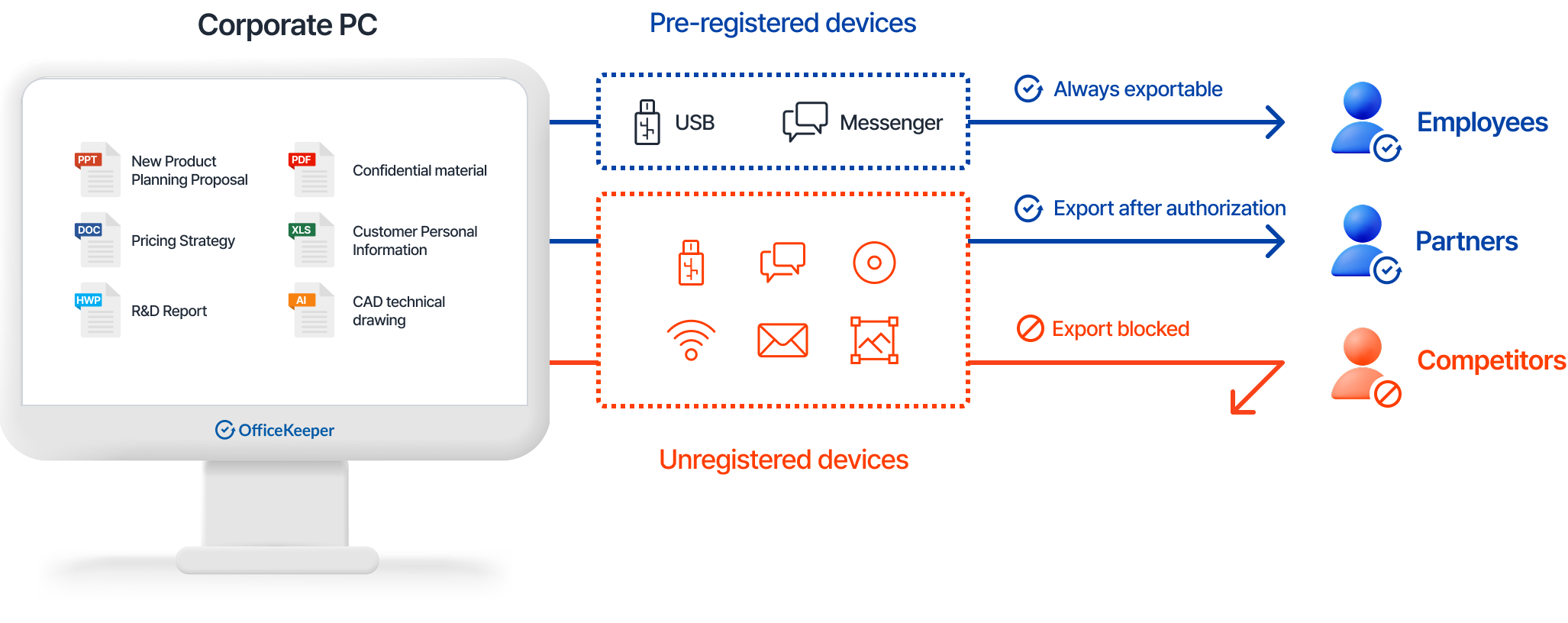
The Data Loss Prevention (DLP) module controls various information leakage pathways and maintains comprehensive logs and original files on the server, preventing data breaches and providing evidence when incidents occur.






Removable Storage Media Control
- Prevent unauthorized copying and export to USB drives, external hard drives, smartphones, and optical media

Internet File Attachment Protection
- Control file attachments via email, cloud services, web browsers, and other internet-based channels

Software File Export Control
- Prevent unauthorized exports through messaging applications, remote control software, web storage, and other programs

Wireless Connection Management
- Block unauthorized internet access through WiFi and Bluetooth connections

Screen Capture/Shared Folder Protection
- Prevent information sharing through screen capture applications and network shared folders

Comprehensive Logging and File Storage
- Maintain detailed logs and original files for all file sharing and export attempts
Data Loss Prevention Process
Administrator Capabilities
Establish department and user-specific data protection policies
Configure permanent export permissions for authorized devices
Manage temporary export approval requests
Monitor all file distribution activities with detailed reporting
Sensitive Information Management
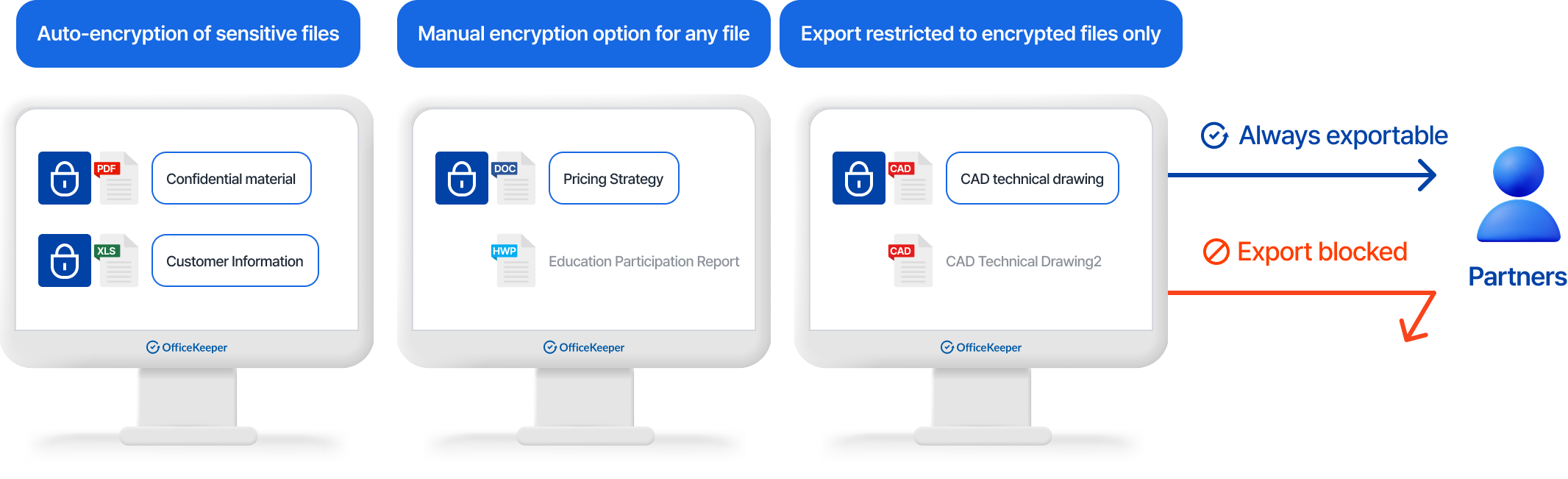
Detect, encrypt, and control sensitive information stored on corporate PCs, including personal data and company confidential information.







Real-time/Scheduled Scanning
- Administrators can scan employee PCs for sensitive information in real-time or according to defined schedules

Automated Encryption/Decryption
- Automatically encrypt files containing sensitive information detected during scanning processes

Export Control Integration
- Prevent export of files containing sensitive information through removable media or internet channels (integrated with DLP functionality)

User-initiated Scanning
- Enable employees to scan their own PCs for files containing sensitive information

Sensitive Data Remediation
- Edit or securely delete documents containing sensitive information identified through scanning

Flexible Encryption Options
- Support both manual and automatic encryption of sensitive documents based on organizational policies
Sensitive Information Management Process
Administrator Capabilities
Monitor creation and modification of sensitive documents
Enforce automatic encryption policies for sensitive information
Control export permissions for encrypted files
Define and update sensitive information detection criteria
Web/Software Blocking
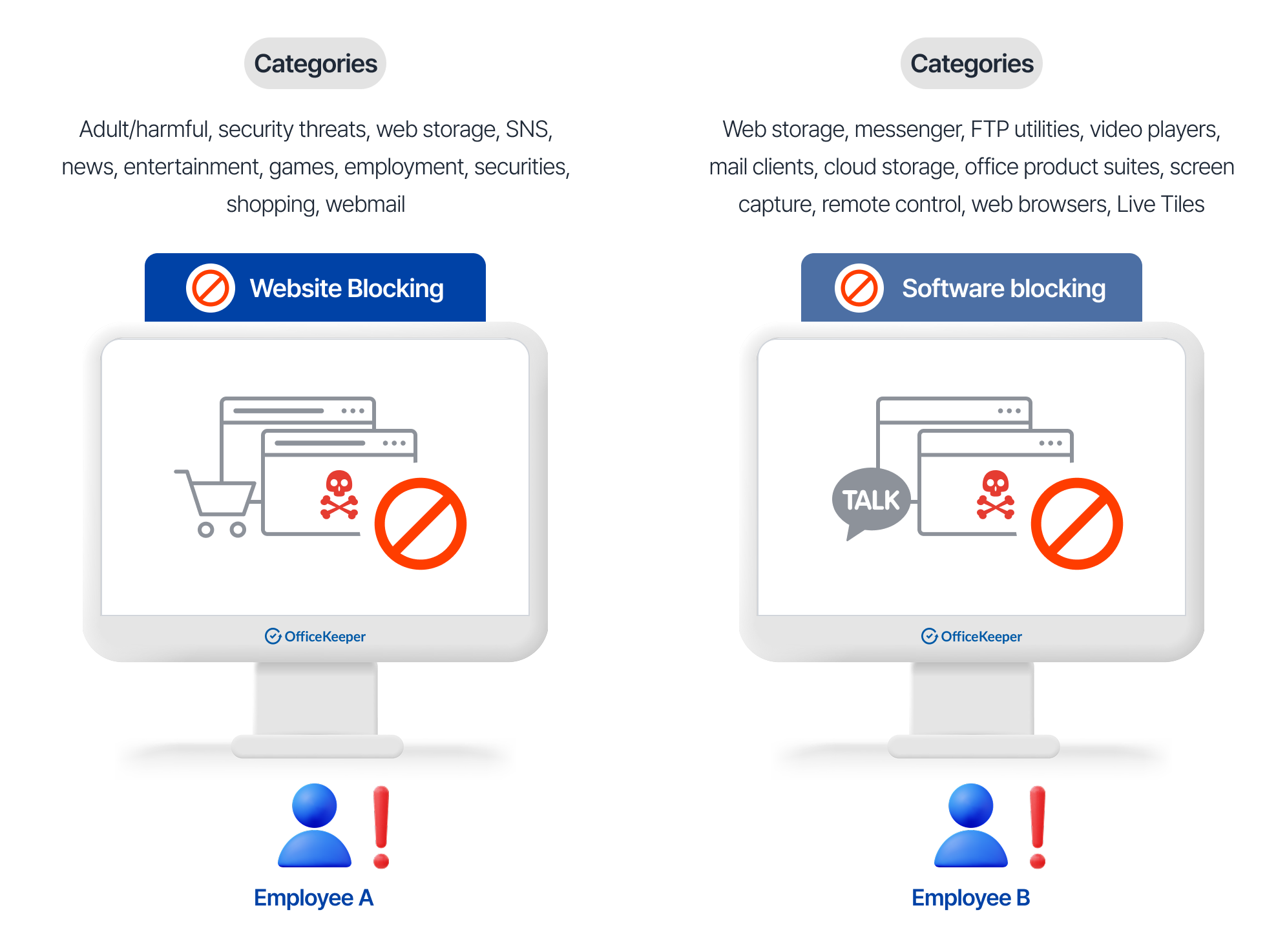
Control access to potentially harmful websites and restrict execution of unauthorized applications to enhance security and improve productivity.



Website Access Management
- Content categorized into 11 distinct categories that can be individually blocked, monitored, or allowed
- Block access to security threats including malware distribution and phishing sites

Application Control
- Software categorized into 11 functional groups that can be individually blocked, monitored, or allowed
Web/Software Blocking Process
Administrator Capabilities
Configure department and user-specific access policies
Block known security threat sites such as phishing websites
Restrict execution of non-work-related software
Monitor all web and application activity through centralized reporting
Print Security
Prevent information leakage through comprehensive print controls and document watermarking while reducing costs through detailed print activity monitoring.





Print Control
- Apply print restrictions based on department, user identity, or document content
- Control printing based on detection of sensitive information patterns or specific keywords

Print Authorization Workflow
- Request exceptions to print restrictions or watermarking requirementsEnable temporary printing authorization after administrator approval

Document Watermarking
- Apply customizable watermarks, printer information, and user identification to printed documents
- Trace printed documents through embedded identification information
- Create and apply organization-specific watermarks based on security policies

Comprehensive Logging
- Record detailed information including printer data, sensitive information detection, and policy enforcement
- Maintain complete printing history for all documents
- Store original print files for audit and compliance purposes
Print Security Process
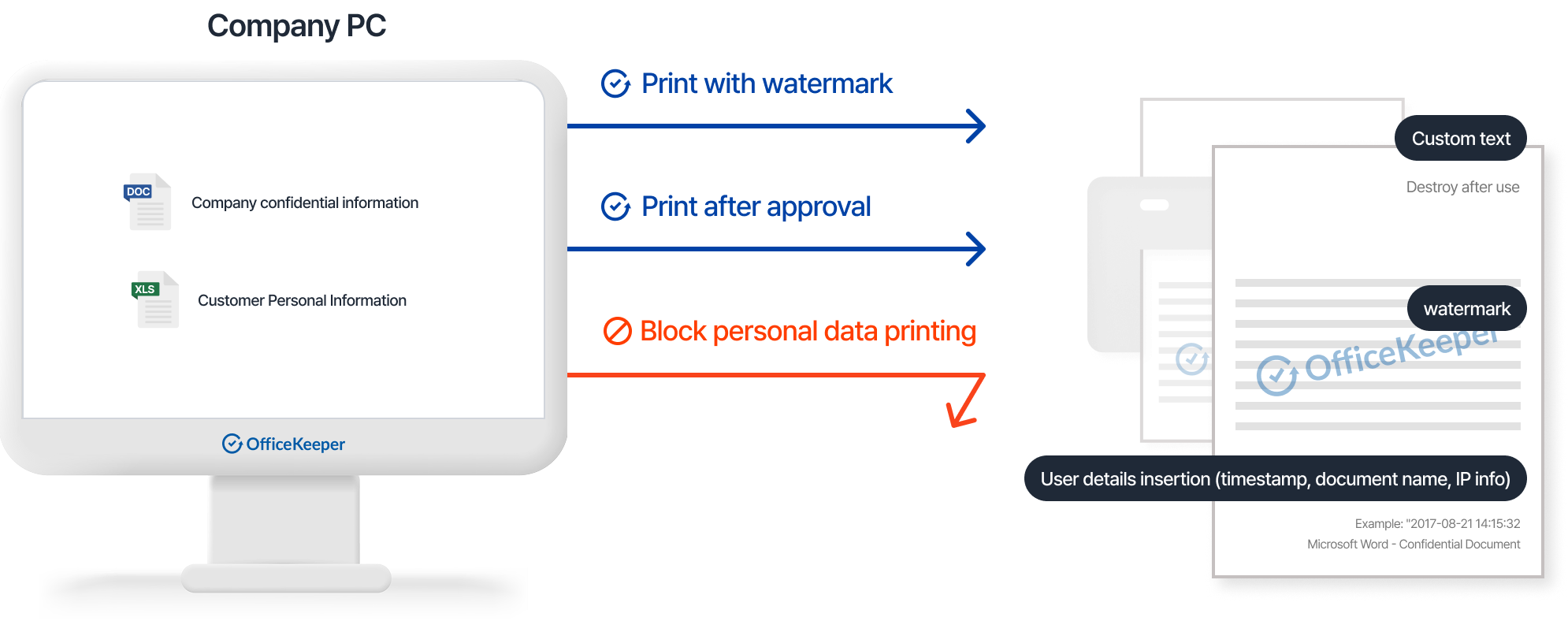
Administrator Capabilities
Documents can be printed with watermarks applied
Documents can be printed after receiving approval
Documents containing sensitive information are automatically blocked from printing
Document Backup
Protect against data loss by automatically backing up files stored on corporate devices and maintaining records of exported files, providing ransomware protection and compliance support.





Automatic Backup of Critical Documents
- Automatically back up important documents stored on company PCs based on file types
- Configure exclusions for specific locations or file types

Export/Print Activity Backup
- Automatically preserve original files when documents are exported via removable media, email attachments, or printing

Version Management
- Maintain up to 10 versions of each file based on modification timestamps

Data Recovery and Compliance
- Restore multiple files to desired versions when data is lost due to ransomware or other incidents
- Provide evidence for information security audits and compliance requirements
Document Backup Process
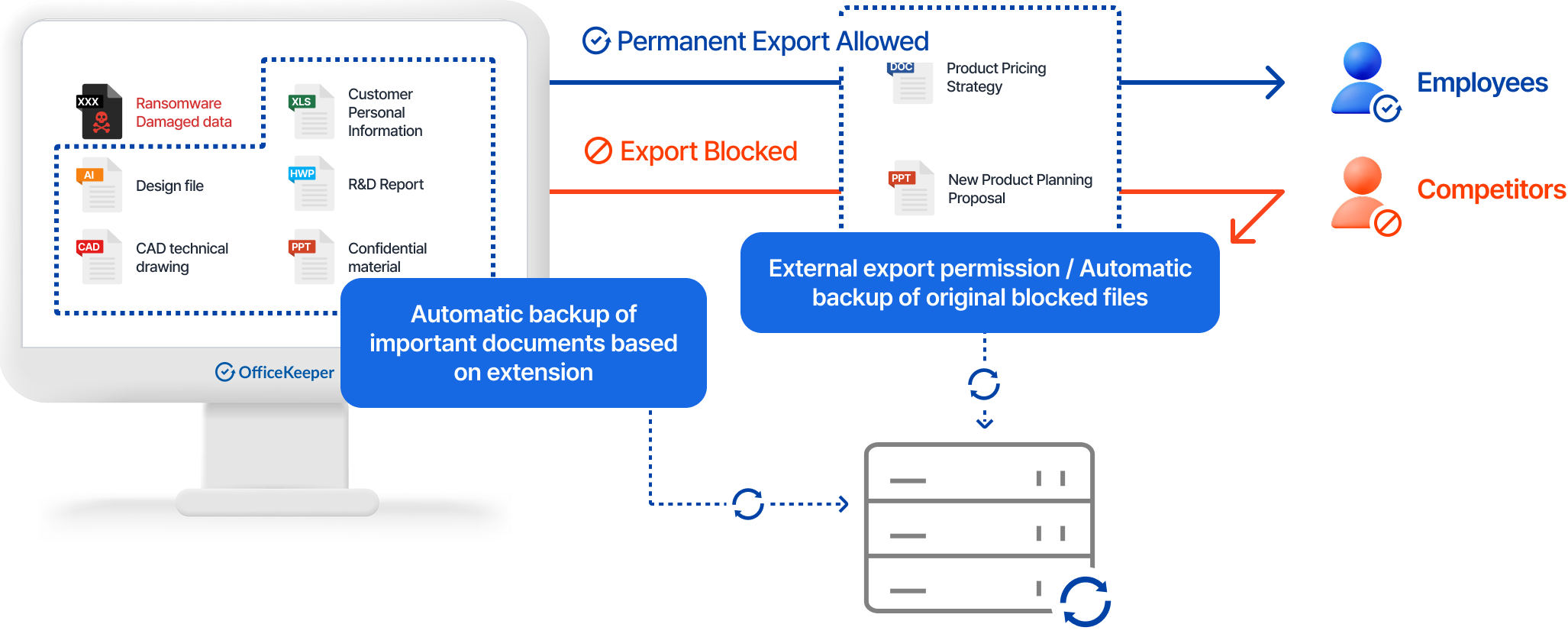
Administrator Capabilities
Configure department and user-specific backup policies
Establish file type-based backup rules
Monitor backup history and storage utilization
Restore files to original state or specific versions as needed
PC Security Assessment
Evaluate and enforce security standards across the organization to maintain optimal protection for all company devices.





Comprehensive Security Standards
- Apply 17 security items recommended by the National Intelligence Service, including security updates and account settings

Security Status Monitoring
- Assess vulnerabilities of company PCs in real-time or according to defined schedules

Automated Remediation
- Automatically correct security issues that don’t meet organizational standards
- Apply forced remediation for 8 critical security controls

Security Reporting
- Generate detailed reports on company-wide security status with numerical scoring
PC Security Assessment Process
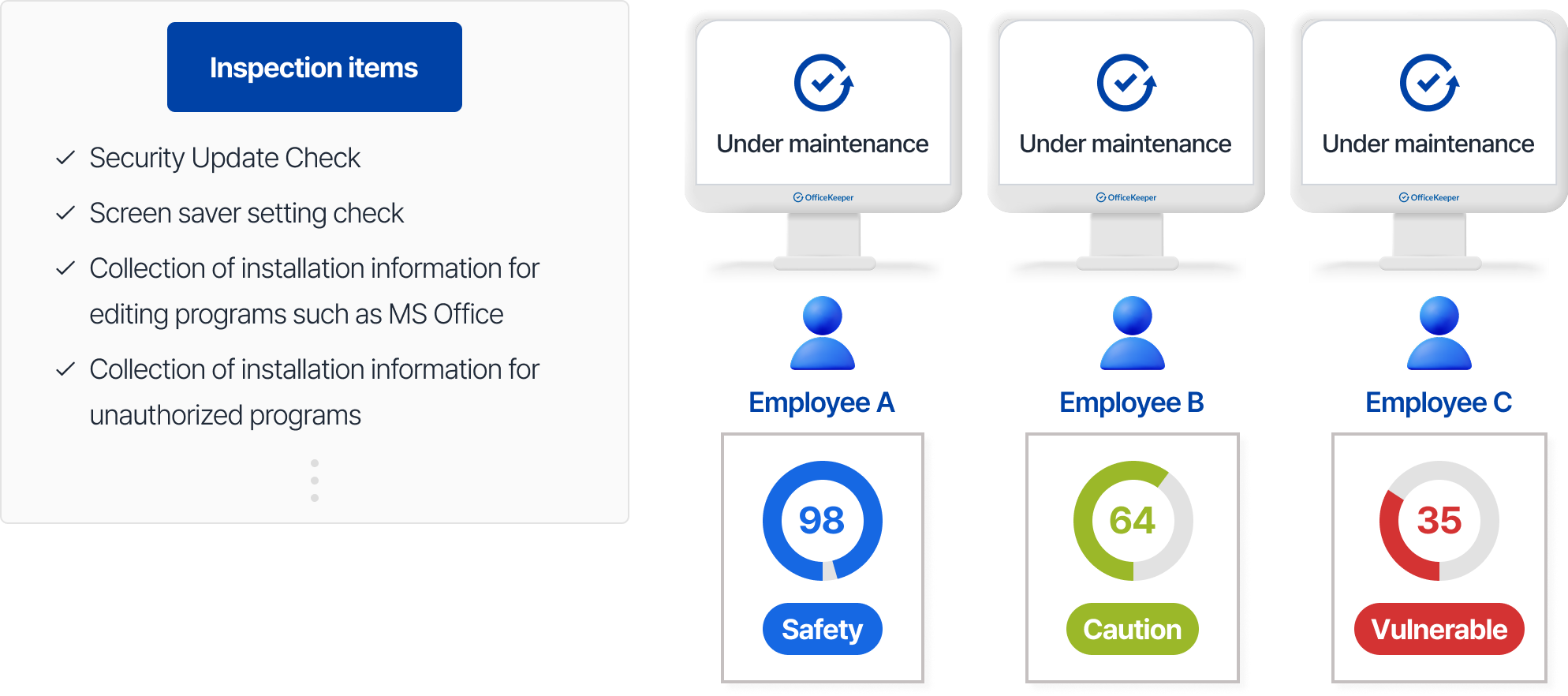
Administrator Capabilities
Schedule regular security assessments
Enforce automated remediation for policy violations
Monitor organization-wide security posture through scoring reports
IT Asset Management
Enhance administrative efficiency with comprehensive management functions for hardware inventory, software licensing, device tracking, and power management.







Hardware Inventory Management
- Track PC and laptop status with complete deployment history
- Monitor storage device changes and hardware modifications

Software License Management
- Track software installations across the organization
- Identify license compliance issues and recommend corrective actions

Device Location Tracking
- Monitor device location through IP-based tracking
- Maintain device movement history for security and compliance

Network Usage Monitoring
- Track IP address assignment and usage patterns
- Monitor network configuration changes

Endpoint Security Management
- Implement automatic screen locking after inactivity
- Enable remote device locking, sleep mode, or shutdown via mobile application

Resource Utilization Monitoring
- Track computer usage patterns
- Monitor device power state history
- Support talent management initiatives through resource utilization data
IT Asset Management Process
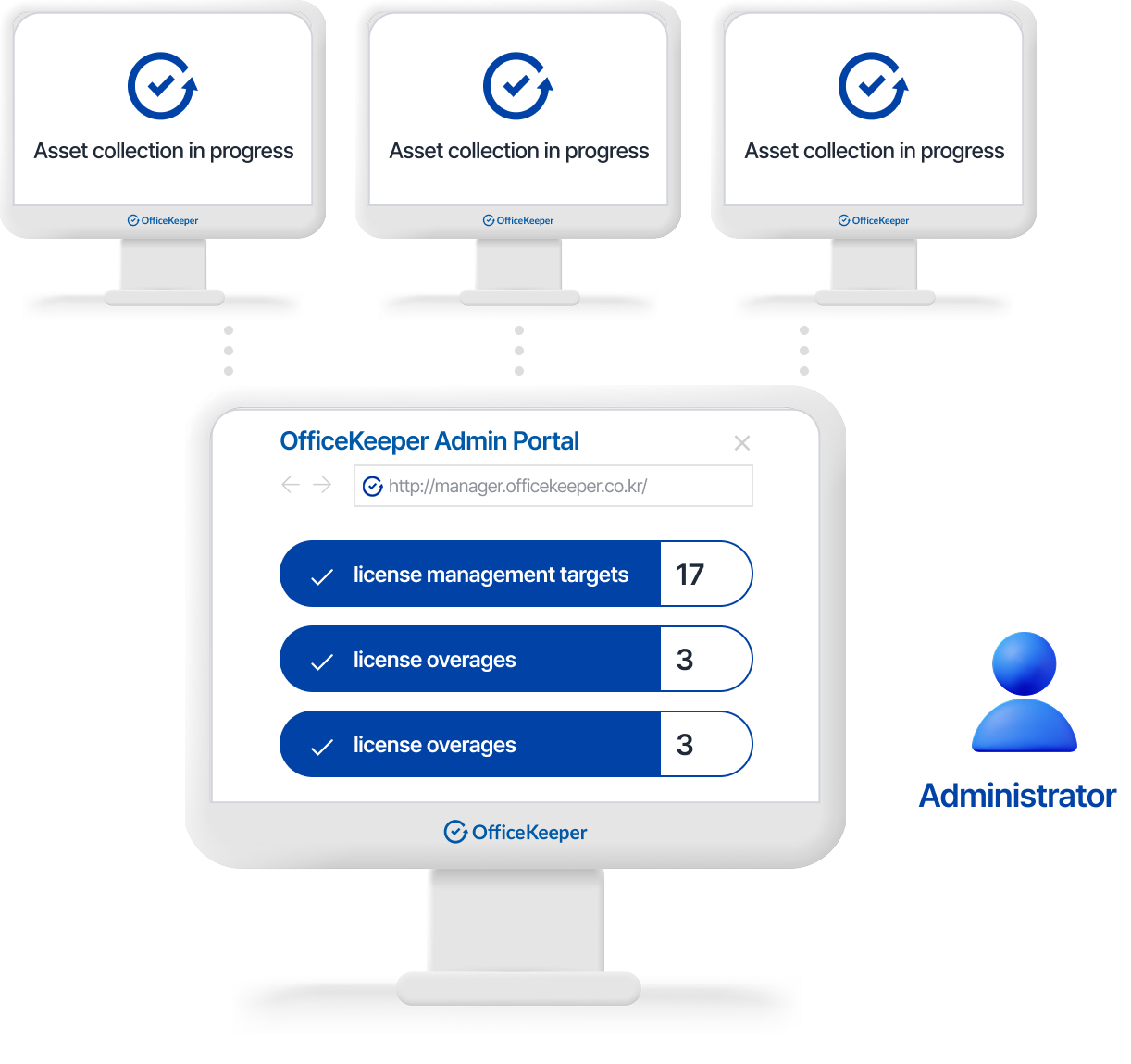
Administrator Capabilities
Automatically collect and manage IT asset information
Track hardware inventory and software license compliance
Monitor device location and usage patterns
Control endpoint power settings remotely
Why Choose OfficeKeeper
7-in-1 Platform: Complete security solution in a single lightweight agent
Intuitive Interface: Easy implementation with minimal training required
Flexible Deployment: Cloud-based or on-premise options for any organization
Cost-Effective: Select only the functions you need
High Retention: Over 90% customer renewal rate
Cross-Platform: Full Windows and macOS compatibility
Proven Technology: 22 patents and national security certifications
The Value of OfficeKeeper
Customer Testimonials
"I've implemented it at every organization I've joined"

"Provides exceptional support for administrative responsibilities"

"Responsive technical support and robust security capabilities"

"We achieved both cost efficiency and effective security management"

"Implemented in just one day when we urgently needed it for a security audit"

"The ability to manage remote branch offices is invaluable"

Trusted by Enterprise Leaders